
Have you ever noticed an old WordPress plugin in your site, or heard news about WordPress sites being hacked through a particular plugin, and wondered if your plugins are vulnerable? Fortunately, there are free WordPress vulnerability databases you can check.
In information security, a vulnerability is a weakness that can be exploited. For example, a WordPress plugin could have an arbitrary file upload vulnerability, which allows anyone who knows how to upload files to your website, which they could use to steal data or damage your site.
These are 3 free WordPress vulnerability databases which you can manually check to see if your plugins or themes are vulnerable.
These databases are often checked by other tools, such as the Wordfence plugin and ManageWP site management tool, for automated checking of your site.
If you don't find results in any of these databases, do a web search for "plugin_name wordpress vulnerability" or "theme_name wordpress vulnerability".
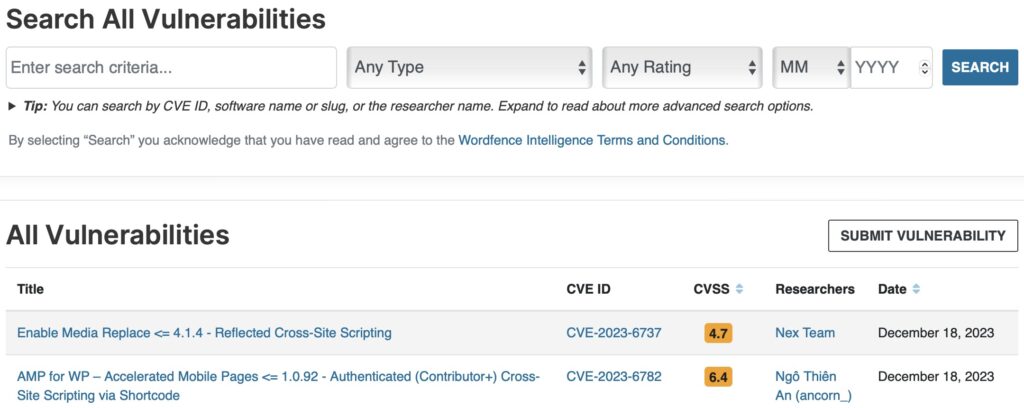
What if you find one of your plugins or themes listed as vulnerable? In many cases, the vulnerability has been fixed in an update, so install that update as soon as possible.
If no update is available, see if the plugin or theme author is aware of the issue and working on an update. You can check the support forum for the plugin or theme in the WordPress plugin or theme directories, or follow links from the plugin or theme page to find the author's website or social media profiles to look for announcements, or to ask about the status.
If you can't find out about the status from the plugin or theme author, or you don't want to wait, you can delete the plugin or theme from your site to remove the vulnerability. Simply deactivating isn't enough; you must delete it. Of course, if you need functionality or design provided by the plugin or theme, you'll need to find a replacement. Make a backup of your site before making any changes.
Going forward, be sure to install updates promptly, especially when they include security fixes.
If you have no desire to sort through WordPress vulnerability databases, then let OptimWise maintain your WordPress site. We keep WordPress core, themes, and plugins updated to stay on top of security fixes, and provide security monitoring.