I use two methods for creating passwords:
Note: This page contains affiliate links. Please see Affiliate Disclosure.
In most cases, a password's length and uniqueness are more important than its entropy (randomness). Why?
Steve Gibson has an excellent explanation on his Password Haystacks page. He says,
The only thing an attacker can know is whether a password guess was an exact match . . . or not. The attacker doesn't know how long the password is, nor anything about what it might look like. So after exhausting all of the standard password cracking lists, databases and dictionaries, the attacker has no option other than to either give up and move on to someone else, or start guessing every possible password.
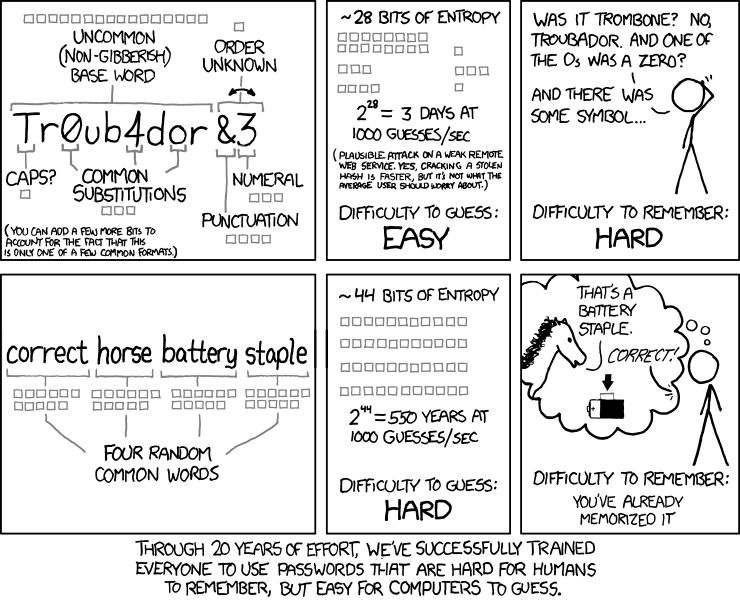
Most security experts now recommend creating passphrases that are long and unique, yet memorable. How? Here's one popular example from the webcomic xkcd, #936 Password Strength:

The xkcd method is approved by security expert Bruce Schneier in Recent Developments in Password Cracking. It's fine to use multiple dictionary words as long as they’re "random", or words that wouldn’t normally be found together. So, you shouldn't use something like "lion witch wardrobe" because those words are frequently found together. Instead, use something like "lion paper auto rose".
Many experts will tell you passphrases like the xkcd one are fine, and they may be right; they know the math better than I do. However, I feel more comfortable using passphrases with uppercase, lowercase, numbers, and special characters because the more character types you use, the more permutations the cracking software needs to try. Some experts feel the same; see the Common Questions & Answers on the Password Haystacks page, and Mark Burnett's Analyzing the XKCD Passphrase Comic. So, you might end up with a passphrase like "lionPaper1auto$Rose". Secure and memorable!